Google Apps is launching two-factor authentication, allowing the capability to verify a person’s identity with a code sent to the user’s mobile device.
Most Web-based services still use systems that require people to sign in to their accounts with a user name and a password.
It’s pretty insecure. People lose their passwords to phishing scams all the time. And traditional two-factor security systems require separate devices such as certificates, smart cards and tokens.
Integrating secure socket layer (SSL) and security assertion markup language (SAML) to use these devices can be complex, to say the least.
Google’s move shows how security verification is moving to the cloud. The value of these cloud-based services came true with VMware’s acquisition of TriCipher, a security and authentication provider. VMware will use TriCipher to connect infrastructures. It provides the capability for single sign-on across different systems.
Here’s how the two-factor verification works with Google. The new system is now available for Google Apps users.
The customer provides their user name and password.
A code is then sent to the person’s mobile device. The code is sent via SMS or a voice call.
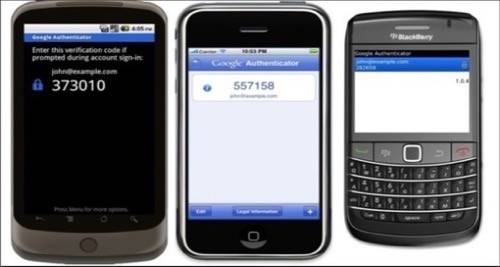
The user then types in the number through Google Apps:
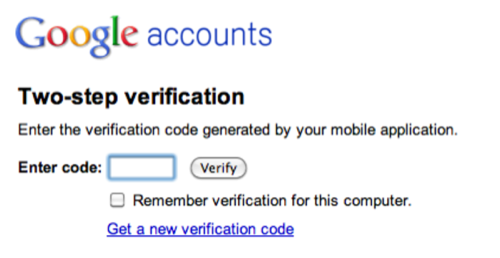
That’s a more modern method for using a SaaS service.
But it’s just a start. The need will intensify as more services ditch user name and password systems. The demand is giving rise to companies like Yubico. The company’s Yubikey product is a USB-key for instant and strong authentication to networks and services. It sends the user’s identity and a secure one time pass code. It works from any computer for any number of applications with no client software needed. Cloudkick is a cloud services provider that uses Yubico.
These forms of two-factor authentication are still pretty rare to see out in the wild. But expect these modern verification systems to be more commonly used as user name and password systems go more out of vogue.










