Today at the cybersecurity conference known as Black Hack, researchers Charlie Miller and Collin Mulliner will present an SMS exploit that could take over your iPhone with just one text. Once the phone is compromised, the hacker would have access to all the functions on the phone allowing them to send email, access your contacts, make phone calls, and of course, send text messages that would send the exploit to more devices.

This serious vulnerability (which apparently Apple sat on for over a month) is probably the first time that most people have heard of mobile phones being used to create botnets. However, this isn’t the first sighting of a mobile phone hijacking attempt for the purpose of botnet creation – a similar exploit was discovered earlier this month. Does this mean we’re on the verge of a new and dangerous trend: the creation of “zombie” phones?
The iPhone SMS Hack
According to Forbes, the SMS exploit being demonstrated at Black Hat today involves sending short, mostly invisible SMS bursts which would allow a potential hacker to entirely take over the phone. The only warning you would have to alert you to the hack would be a text messaging that contained a single square character. If you received something like that, your only recourse would be to turn the phone off immediately.
The researchers said they alerted Apple to this vulnerability over a month ago, but no patch has been released. Apple isn’t returning calls requesting a comment, either.
The First Mobile Botnet?
Assuming the iPhone exploit described above was able to make it into the wild, it could effectively compromise all the unprotected iPhones in the world (which, in theory, would be all of them, if no patch is distributed). The hack would essentially turn the phones into “zombies” – a term usually used to refer to PCs compromised by a hack, virus, or trojan horse in order to do the bidding of a hacker. Along with other compromised PCs like them, this group of computers would form a botnet of “zombie” machines.
While botnets are common in the PC world – it’s estimated that these machines are used to send anywhere from fifty to eighty percent of spam worldwide – botnets consisting of mobile phones are practically unheard of…or are they?
Earlier this month, Symantec revealed an SMS threat dubbed “Sexy Space” created using malware known as SymbOS.Exy.C, a revision of oldervariations also used to create similar threats. Using simple social engineering tactics, this hack involves sending SMS spam with names like “Sexy View,” “Sexy Girl,” and “Sexy Space” to encourage victims to click an included link in the text message.
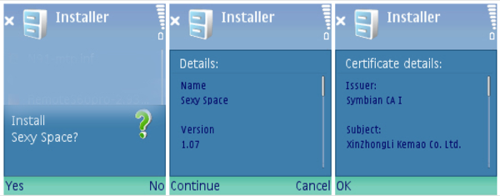
This particular exploit, only found on Symbian-powered devices so far, is smart enough to end certain programs on the hijacked phone that would make it possible to manually end the threat. At first, the hack was only being seen in China, but later an English version was discovered in the Middle East.
What’s most frightening about this particular threat is that it’s controlled by a central server. That means hackers could control the attacked phones the same way hackers today control zombie PCs. This led the Symantec researchers to wonder if this was, in fact, the first case of a mobile botnet being spotted in the wild.
But My Phone Has Never Been Attacked!
Security researchers have been warning us about the upcoming mobile risks for some time and yet few people have ever actually had their phone compromised by malware, it seems. To date, mobile exploits have been few and far between and have had no major impact on the industry as a whole or on consumer confidence levels regarding these devices. Perhaps lulled into a false sense of security since mobile phones were once much more basic devices without internet access and data plans, most people don’t even realize that their phone could be at risk of an attack.
In a paper released this past fall from the Georgia Tech Information Security Center, Tom Cross, a researcher with the IBM Internet Security Systems X-Force team was quoted as saying how surprised he was that there haven’t been more attacks to date on smartphone devices like Apple’s iPhone. However, he noted that “financial motivation and increased adoption will increase attacks to smartphones in the years to come. As more payment infrastructure gets placed on these devices, they will become a more attractive target.”
In other words, mobile phones just aren’t worth hacking yet. That will change once more financial transactions take place over phones, agreed Dave Amster, VP of security investigations at Equifax, in that same report. “Consumers are ordering credit reports from their Blackberrys, which puts valuable information at risk,” he said.
Still, hacking the mobile platform will remain a challenge. According to Patrick Traynor, a computer science professor at Georgia Tech and member of GTISC, the lifecycle for mobile phones is much shorter than that of PCs. Most people buy a new mobile device every two years – a cycle which allows manufacturers to keep up with security design – and potentially stay ahead of hackers.
But if there’s one thing we’ve all learned over the years, it’s that you should never count out the hackers. If there’s something to be gained by creating mobile botnets – beyond simply proving that it’s possible to do so – then there’s no doubt that hackers will attempt to create them.










