Before everyone panics, let’s get one thing clear: the new Twitter worm is only a proof-of-concept devised by computer security researchers at Secure Science – it is not out in the wild. That said, its very existence should raise some questions about the state of security at Twitter – something that’s more important than ever given how rapidly the service is becoming mainstream. This latest security concern involves an attack, similar to the clickjacking incident from last month, that takes advantage of a web programming error on Twitter’s support site. The result of the attack would force users to post unwanted messages to their Twitter stream. If those messages were combined with malicious code, “this could even be used to take control of a victim’s computer,” says Lance James, chief scientist of Secure Science.

The Potential Threat
The attack, posted online here, first displays a warning message and then posts Secure Science’s test code “@XSSExploits I just got owned!” to the victim’s profile. But if a hacker wanted to use this technique to compromise users’ PCs, they could remove the warning screen and combine the link with a sensational message which users couldn’t help but click. Add in some browser attack code, and before you know it, clicking a Twitter link could allow a hacker access to your computer. This, says James, “would just tear the cr*p out of Twitter.” He adds, “I’m holding my breath, hoping no one does something stupid at this moment.”
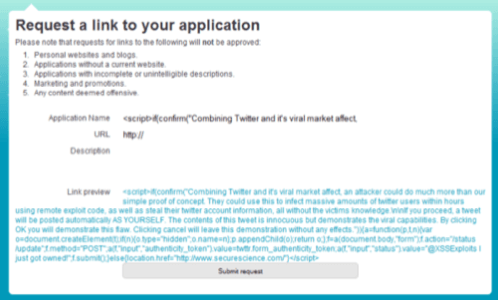
According to Secure Science researchers, this particular bug can be eliminated by fixing the cross-site scripting flaw, but if another similar bug were to show up on the site, users would soon face the same problem all over again.
Still, one has to wonder, why are they publishing this information publicly instead of alerting Twitter directly? Apparently, it’s because the research company is concerned Twitter is not taking security seriously enough. James says he hopes this demonstration will push Twitter into making it more of a priority.
The State of Twitter Security
It’s easy to see why security professionals may be worrying about the state of security at Twitter – the company has had some rather high-profile incidents as of late. Only last month, a second clickjacking attack was revealed after the company had just finished patching one that was unveiled in January. Also in January, the accounts of 33 high profile Twitter users including Britney Spears, CNN news reporter Rick Sanchez, and Barack Obama, were compromised by hackers who defaced their accounts with embarrassing and offensive messages.
At the time, Graham Cluley, senior technology consultant at Sophos advised Twitter “to take a long hard look at its security to ensure that this never happens again, and regain the confidence of its members.” Yet since then, more potential attack vectors have been revealed.
Staying Safe on Twitter Keeps Getting Harder
If Twitter is indeed replacing, or at the very least, augmenting email for interpersonal communications, then perhaps it’s time for us to apply those same age-old rules that once applied to email – be careful what you click. Now that it’s finally been drilled into people’s heads that email attachments aren’t always safe, it seems like we have to start again educating Twitter users that the same goes for links.
But when a service goes mainstream – like Twitter is doing now – it’s going to become filled with people who won’t give a second thought to security concerns such as these. Instead, without intervention on the part of Twitter to address these issues, consumers are going to end up learning “the hard way” – by becoming victims.
The security problem only gets worse when you think about how easy it is for people to create fake celebrity accounts not to mention how easy it is for Twitter spammers to join the service. Since Twitter doesn’t authenticate new accounts via email, anyone can post any message from any address, real or fake. There are even opt-in services that Twitter spammers can join to quickly accumulate large numbers of followers quickly in an attempt to appear more legit.
Although Twitter is attempting to fight spam on several fronts (they’re now disabling accounts that automate re-following for instance), it seems as if more and more Twitter spammers are creating accounts every day. (How many of those SEO advisors and ‘life coaches’ are for real, I wonder?)
As Twitter explodes into the mainstream, it may be time for them to work on addressing some of these issues before they focus on enhancements to the site like the relatively new “suggested users” section or the in-house ads – features which a few folks suspect may have something to do with Twitter’s supposedly soon-to-be-revealed business model. While we understand the service needs to develop their business plan, they recently closed a $35-million financing round, which added even more cash to their previous round ($15 million). Given that they only have 20 employees, they’re (in theory) only burning through around $5 million a year. We’re not sure what Twitter is doing with all that money, but we would like to suggest that they use some of it to hire security professionals to help make the service safer…before it’s too late.










