Connected devices may be the biggest security challenge we face over the next several years. Companies are keen to analyze user IoT data to better understand consumer behavior and are sometimes gathering more data than they need for their service. But what are the potential consequences to your customers, and your company, if this personal info is stolen or accidentally released? What happens when a criminal uses this information to stalk someone online?

With so many IoT devices, apps, and services coming to market, more and more personal info is being captured, transmitted, and stored, yet much of this data is unnecessary to support the functionality of the device or service. You may think this is not a big deal, but the more personal data you have, the more resources your company will have to devote to protecting it. If there is a breach, the bad guys can extract a large amount of personal information about customers. The potential consequences range from identity theft and fraud of your customers to significant financial damage to your company’s brand.
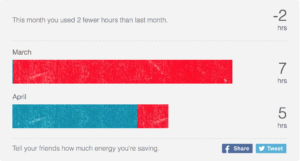
Once a month I get an email from my thermostat service, telling me how I compared to the previous month, to my neighborhood, and what external factors may have caused my energy use to change. This is valuable info that does not violate my privacy, and if I want to share it there are Facebook and Twitter buttons on the infographic. Even if I choose to share it publicly, there is no info that would give away my location, or when I am away from home.
Compare this to my fitness wearable, which wants to post to Facebook for every workout. While this is probably done for good reasons to help encourage and reinforce my exercise regime, it releases potential info on when I am at the gym and not at home.
When developing a new device or service, make it better by collecting less data. Instead of gathering everything you can possibly think of, determine what minimum data is required to deliver your service. Pay special attention to items that constitute personally identifiable info, and ask why they are needed. These include:
- Full name and address
- Document numbers, such as social security, passport, or driver’s license
- Credit card or bank account info
- Date of birth
- Biometric data, including photographs of the face
- IP address or other session identification details
One of the most common ways of identifying an individual is via a username and password. It’s been around since almost the inception of the digital age and is a constant source of concern as we see an increasing number of high-profile breaches exposing usernames and passwords. An emerging authentication alternative is using multiple factors such as your fingerprint and your device location to create a one-time token to authenticate a specific transaction like a banking or retail purchase online.
For IoT data, tokens improve security
This would be used instead of relying on usernames and passwords. These tokens only exist for the time to complete your specific transaction and are not vulnerable to a brute force attack, and cannot be reused even if they are stolen. Moving to single-use tokens greatly improves the security of your interactions.
Tokens can be validated more easily than a complicated password encryption, reducing login time, and the password is not stored anywhere else and does not travel outside of your most secure systems. In the event of a breach, any stolen tokens are useless for authentication and do not enable the attacker to calculate the next valid token. In the spirit of doing more with less, think about embracing authentication tokens instead of usernames and passwords.
With so many new devices and services coming to market, it is necessary to safeguard your business and your customers. Connected devices should not collect, keep, or transmit more data than they need to operate the service, especially personally identifiable information. There are multiple companies doing this right, which delivers value to me as a consumer while also gathering useful data for their own use, without revealing personal info.