
The proliferation of mobile devices has created a firestorm of demand for Application Programming Interfaces (API) to act as data gateways between devices and services. But fire can also be a destructive force, and mis-managed APIs can hurt application performance, alienate developers and even lead to costly and damaging data breaches.
API Security Is Critical
Among other things, APIs serve as gateways to Web-based services like Twitter or Facebook. They are the specifications that let developers build applications that communicate directly with those services. You can think of APIs as doors; they let data in and out of a Web service. Just like physical doors, leaving APIs open can let anyone wander in, for whatever purpose.
APIs are only as secure as they are written to be, explained Alistair Farquharson, chief technology officer for API-management vendor SOA Software. Smart developers make sure their APIs are open only for those people who have the authorized key.
What Problems Can APIs Cause?
The threat assessment for an API that isn’t locked down isn’t a pretty thing. Insecure APIs can fold under the artificial pressures of distributed denial of service (DDOS) attacks (which attempt to overwhelm a site or service with spurious requests in order to block legitimate access) , blocking the door through which data from a Web service is supposed to flow – perhaps bringing down the entire site. SQL script injections (which attempt to insert malicious code into a database), Farquharson added, could be used to re-route or copy data to outside servers operated by people who have no business looking at your data or your customers’ information.
Because APIs enable very deep leveraging of a web service’s features, they can be misused by hackers to spoof services, or even pretend to be entire websites, as web designer Feross Aboukhadijeh detailed last Autumn, when he discovered how the HTML5 Fullscreen API could be abused to appear like any legitimate site, such as a banking transaction web site. Aboukhadijeh works through how the fake web site could be created and fool many unsuspecting users, even down to a citation of a study on “change blindness,” a psychological event where people can miss obvious changes.
And then there are the less subtle attacks, such as the 2008 security breach that took advantage of a bad Myspace-Yahoo services API and ended up gaining access to celebrity photos that were supposed to be privately stored.
These are the obvious malicious outcomes of APIs that aren’t secured properly. But hacked APIs can also create perceptions of poor quality of service, which could erode customer confidence in a Web service.
The importance of getting APIs under control can’t be overemphasized, contended identity-management vendor Xceedium‘s VP of Product Management, John Suit. “If the web interface is the front door to a company,” Suit said, “then the API is the side door.” And any door that lets in the wrong person – or the wrong code – can result in the same disastrous results.
Building A Better API Lock
Locking down APIs can tricky business. In these early days of the API boom, there are many different API standards being used by vendors to create the APIs through which applications will leverage Web services. Complicating that is the fact that there are a lot of different security standards, too.
This is a rich recipe for problems, since an effective API management system must allow authorized developers in to use the API, but not let anyone gain so much access they can subvert the API or use it as a doorway to the host service’s internal data. Oh, and add to that mix the problem you have if APIs have to reside in a public cloud environment, outside your firewall.
Most security experts recommend using some sort of the strong authentication process in place when working with APIs. You need to make sure that the absolute correct person is accessing the API.
SOASoft’s approach is a just-launched API Gateway virtual appliance that uses an OAuth server to work with many different existing security protocols. Playing to its strengths, Xceedium uses role-based identity systems to not only make sure the right person is connecting to the API, but that person should be accessing that API in the first place.
Things To Do Right Now
Even if you don’t want to implement a formal identity and security management system for APIs, there are steps to take right now that will at least help mitigate potential problems.
If you want to prevent SQL injection attacks, then by all means sanitize the inputs in the API that connect to your internal databases. This will reduce the risk of a successful attack of this kind:
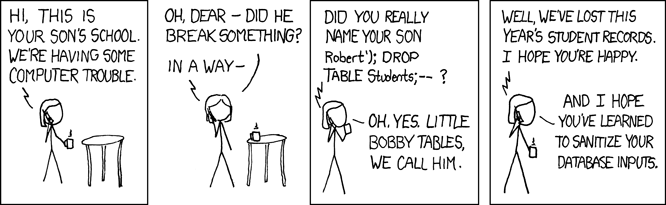
API developers should also make sure that everything is transmitted through the Secure Socket Layer (SSL) – encrypted and transmitted by HTTPS – so that information like usernames and passwords are not captured in-process and then used to gain access to users’ accounts or worse, the host organization’s account.
APIs are becoming increasingly important as so many new devices on the Internet generate and consume data via an ever-expanding list of Web services. While essential, those APIs also creating tempting targets for hackers. The need to lock down this growing vulnerability has never been a higher priority.
Lead image courtesy of Shutterstock, comic courtesy of XKCD.










