
Guest author Vijay Dheap is a Mobile Security Strategist at IBM.
Security is a balancing act, especially when it comes to emerging technologies that promise to unlock massive business potential. Each new wave of change requires an enterprise to adapt its security posture, or risk being left behind – or exposed to unmanaged risk.
Mobile is no different.
What was predominantly a consumer-oriented phenomenon is rapidly becoming a top business priority. Individuals, product teams and marketing departments are all scrambling to seize the benefits mobile presents, while security organizations are scrambling to regain control – or at least awareness – of all the enterprise’s mobile-related activities. Enterprises recognize that going mobile requires a strategic perspective.
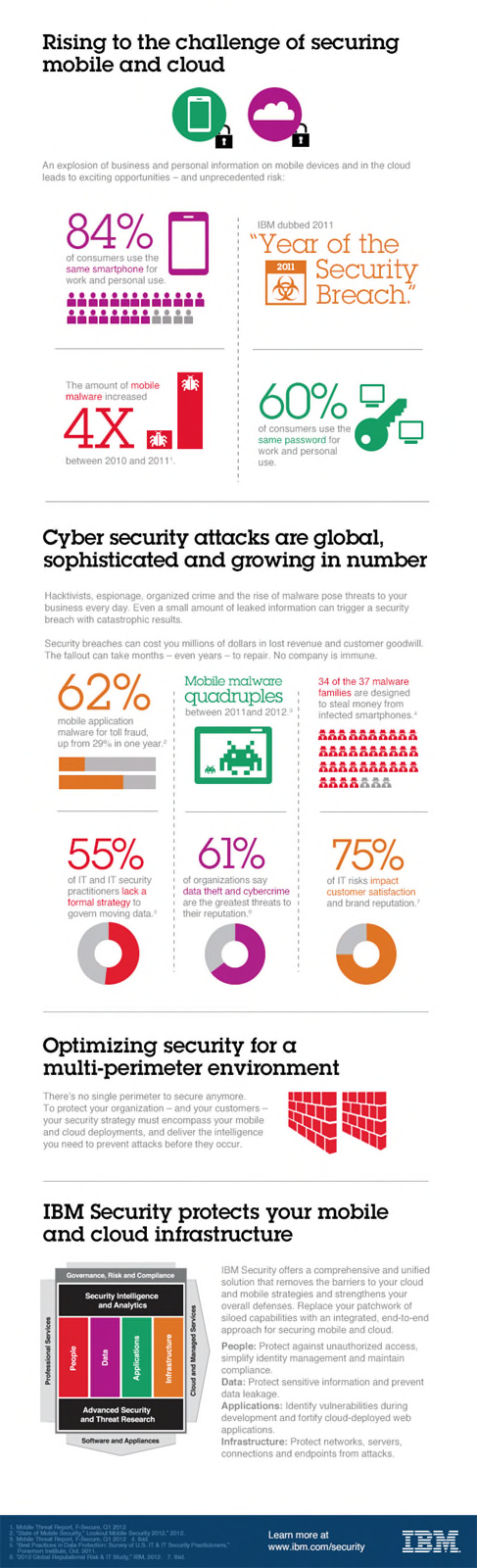
The importance of defining a security strategy for mobile carries greater urgency than ever. While 84% of consumers now use their personal smartphones for work, mobile malware has increased more than four times since 2010. Recent reports indicate that 51% of companies have experienced data loss due to insecure mobile devices – and the average cost of a breach was a hefty $5.5 million. Enterprises have a very real need to reduce this risk while not affecting business objectives focused on mobile. (For a visual look at mobile security stats, see the infographic at the end of this post).
Given the dynamic nature of the mobile market, it can be difficult for an enterprise to define a mobile risk management strategy. Organizational inertia alone can lead to increased risk. One approach is to concentrate on four focus areas of mobile security:
- BYOD
- Protected Access
- Secure Mobile Solutions
- Mobile Security Intelligence
1.BYOD, or Bring Your Own Device, has become a defining characteristic of mobile adoption in the enterprise. While not exclusive to smartphones and tablets, these new devices led the way with rapid, organic penetration of many enterprises. But every organization can customize the policies that govern the use of employee-owned mobile devices within the enterprise. BYOD policies should reflect the organization’s risk appetite based on its industry, regulations and culture. Policies can modulate the degree of device choice and which employees participate. Of course, before it can enforce its BYOD policies, an organization needs to gain visibility and control over these new devices.
2. Protected Access: Mobile devices empower employees to access relevant information whenever they need it. No matter how much enterprise data is stored on the device, users will frequently need to access additional enterprise data and resources. The enterprise must not only establish secure connectivity channels but also manage risk associated with user authentication and authorization. Given that mobile access typically takes place predominantly outside enterprise boundaries, special care is needed to prevent unauthorized access and reduce risky behaviors. Plus, protecting mobile access provides security teams another lever to gain awareness over their mobile audiences even when they cannot have visibility over the devices themselves (i.e. consumers, partners and unmanaged employees).
3. Secure Mobile Solutions: Apps have emerged as the primary interface for delivering mobile solutions to consumers, partners and employees. Apps enable the rich, task-oriented functionality and user experience that mobile consumers demand. Some mobile solutions are outsourced, while others are built by various parts of an enterprise. Security design needs to be incorporated in each step of the software development lifecycle. Mobile app developers – who are generally not particularly security aware – need tools and processes that help them bake in the enterprise’s security standards and best practices. And the enterprise must also enforce a baseline of security standards across the entire range of mobile solutions it develops.
4. Mobile security through risk management requires constant vigilance. With rapid innovation comes new capabilities that promote new behaviors. And as mobile adoption accelerates, it becomes a richer target for attackers. The threat landscape indicates a growing affinity towards targeted attacks at individuals or organizations, leveraging mobile as a primary socialization platform. To identify risks and take appropriate mitigation steps, enterprises need to gather intelligence across all the touchpoints of mobile engagements. Intelligence gathering should include aggregating security events from the device, users, apps and the network for analysis – including tracking compliance with existing risk management policies.
Mobile is a transformational technology giving individuals unprecedented freedom and flexibility in how they engage professionally and personally. Enterprises cannot afford to ignore that opportunity, but can’t put themselves at risk in their rush to embrace the new technology. By focusing on BYOD, protecting access, securing mobile solutions and developing mobile security intelligence, enterprises can balance the risks and rewards for individual workers and the organization as a whole.
For more on mobile enterprise security, see the infographic below.
Lead image courtesy of Shutterstock.









