The conventional wisdom has been that industrialized hacking organizations have become particularly successful with social engineering – coaxing employees into doing something stupid that unlocks their networks’ security. Analysts at the RSA Conference in San Francisco last week spoke of increasing incidents of telephone calls – actual human beings from call centers, pretending to be “Windows Security” or some other service, offering to help employees eradicate a non-existent virus from their systems and asking for their passwords outright.
If such incidents are indeed increasing, then they were no match last year for a staggering rise in external threats directed against data center servers. This according to data pre-released last week by Verizon and given to select reporters, in advance of the carrier’s annual Data Breach Investigations Report. As the report’s director of research and intelligence, Wade Baker, told ReadWriteWeb, data collected from its own security investigative team’s caseload with Verizon’s own enterprise customers – which include the U.S. Secret Service – shows some 92% of threat agents contributing to security events were discovered outside the firewall.
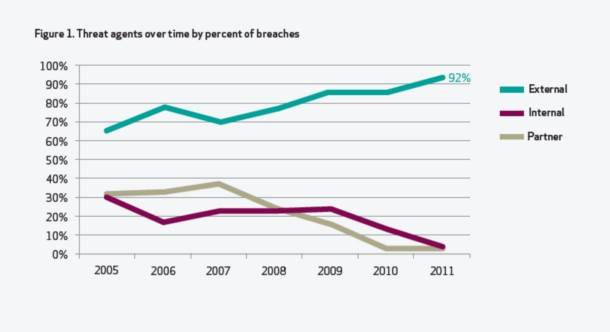
“Since 2005, it’s pretty obvious that attacks are becoming external in nature,” stated Baker in a news conference. “By external, I mean the threat originates from outside your environment. It is not an employee of your organization. Yes, they commit crimes too, but by and large, we see these increasing attacks stemming from the outside.”
The Verizon team’s investigation revealed that servers were targeted by 90% of the threat agents identified in some 90 breach events throughout last year. Baker said it’s obvious that the objective of attacks now is moreover to acquire data rather than to disrupt systems and services. While about 49% of threat agents also targeted “user devices” – which in Verizon’s classification includes PCs, tablets, and smartphones – a vast majority of that targeting was intermediate, a way to eventually get at the server.
Are the user devices in this class comprised of “BYOD” devices, which were the subject of many separate sessions at RSA 2012 – devices that companies allow their employees to bring inside and connect to the network? And if so, are those considered external or internal agents? I asked the report’s contributing risk analyst, Marc Spitler, who told me that if an employee device were connected to the network contrary to policy, then it would be classified as an internal agent – the class which Verizon perceives as a less significant threat component. “I don’t know if we actually did see bring-your-own-devices as the ‘Patient Zero,’ if you will, of a malware outbreak,” said Spitler.
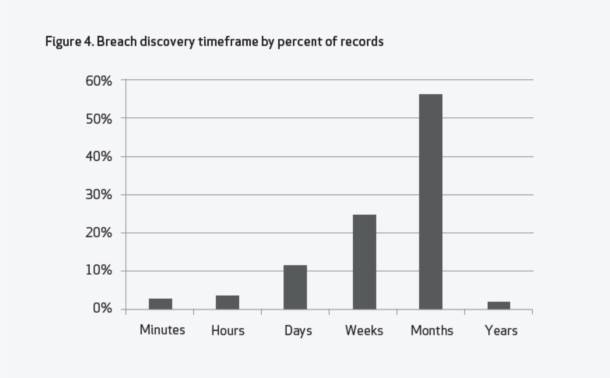
A potentially more disturbing statistic from the report, which Verizon shared with reporters in advance, concerned the elapsed time between the actual attack incident and the discovery of its having taken place. “Most of the time, it takes months,” Baker told reporters. Backdoor tactics have regained favor for evading discovery, he said, having been utilized in 26% of investigated incidents. “And to be honest, the capabilities of the victim are pretty terrible sometimes. We’re not seeing a lot of maturity in this space.”
Verizon also previewed this bit of data: Some 29% of threat incidents involved the ability to guess a user’s password correctly. In the wake of Windows 8 tying together a variety of cloud services under an arguably guessable, single Microsoft Account password, I asked Baker whether this percentage was likely to go up in 2012.
“There’s a balance to be struck between usability and security,” Baker responded. “The reason we do single sign-on is because it’s highly usable. I don’t want to sign into 15 different accounts on my computer; I want one password that lets me not remember all these different things. Of course, there is increased risk, and there’s a security trade-off in doing that. It would be best to do something different with every single place that you sign in. So yes, it’s going to get [to be] more and more of a problem, because we’re integrating more things. And it’s also more of a problem because the attackers seem to have picked up on this.”
Baker noted that Verizon’s Top 10 list of threat actions, over the last five years, have shifted towards authentication and authorization. I asked him what organizations he’s seen that use three-factor authentication to address this issue. He answered perhaps none, but added that the reason for this could very well be because Verizon deals with companies whose systems have already been breached – and maybe three-factor systems aren’t among them. “It seems like there’s been such a big push to get a good two-factor system set up, in many cases, that three and more is pretty rare.”