The company is called CrowdStrike (not “CloudStrike”), and most folks attending the NSA session featuring the company Wednesday morning had never heard of it. That wasn’t why they were there. The man behind CrowdStrike is George Kurtz, the former chief technology officer of McAfee, and the man widely credited with bringing that company into the realm of seriousness.
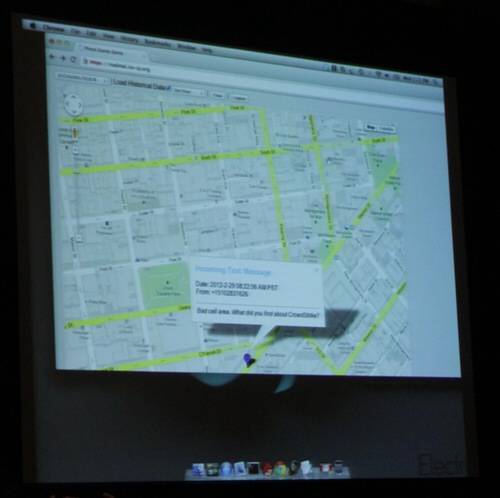
During the session introducing attendees to his new venture in a very big way, Kurtz demonstrated the threat of mobile remote access tools (“mobile RATs”), capable of polling smartphones to determine their users’ location and scope their transactions. “It’s the ultimate spy tool, and it travels around with us at all times… If you haven’t figured out privacy’s dead, this’ll kill it for you.”

Kurtz painted a picture of history repeating itself – of the first wave of RATs, akin to the Back Orifice tools of the 1990s. His technology officer, Dmitri Alperovich, conducted a live demonstration of a mobile malware tool that has actually been in the wild for about six months. Its use in the new hack is to deliver an end-to-end “Chinese RAT.”
In the re-enacted scenario, Kurtz’ associate demonstrated using WebKit, the Web browser engine used by Apple Safari and Google Chrome, also found in the latest versions of BlackBerry OS. Google’s Dalvik, which serves as its Java-like virtual machine, runs WebKit on Android phones. The vulnerability targeted is in Android Froyo, version 2.2.x, which is not the latest version but one of the more prevalent.
“We wanted to show what a target adversary could do,” said Kurtz. So rather than going bug hunting, the exploit team purchased some 20 low-cost “half-day bugs,” for a total price of USD$1,400. Using these bugs, the team developed a set of exploits. Kurtz reminded the audience that if they could not develop these exploits, they were not dealing with retailers willing to give them their money back. They needed to trigger local privilege escalation vulnerability, which is actually a publicly available vuln that required no monetary expenditure.
Alperovich admitted that the “weaponization” of the exploit was not as easy as originally considered. The first challenge was to modify the program counter on the ARM processor, in order to make it point to the malicious shelf code. Then it needed to inject payload into the heap space. Typically in a vulnerability exploitation, you have a minimum of memory in which to inject the Nickispy APK. This is the repurposed “Chinese RAT” that is available in the wild. Reliability was a concern, Alperovich added, so quality assurance processes were employed.

“WebKit is not an easy platform to exploit. It has multiple heaps, so it took a lot of magic,” he noted.
The root exploit was used to elevate privileges and activate the malware. This requires a reboot, which must be triggered automatically. If you’ve ever noticed your Android phone rebooting itself, you might want to take heed.
“We’ve done this before,” said Kurtz, “but not necessarily in this small a form factor.”
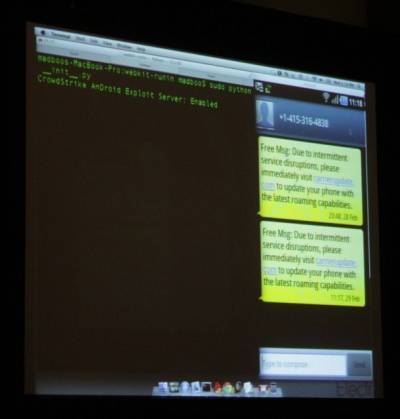
For the exploit to work, someone sends Kurtz an SMS (not an e-mail, which can be subject to corporate filters), stating there’s been a service outage, and asking the user to click on this link to download roaming information to overcome the outage. “For a buck or two, you could send a spoofed SMS message,” said Alperovich.
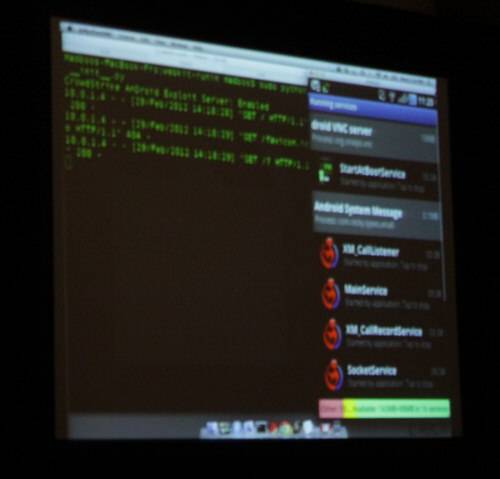
When Kurtz clicks on the link, the delivery mechanism is running on his phone, but it needs to escalate privilege. The method chosen is vold, which is normally used to tell Android that a USB device has been attached and to trigger a driver. After privilege is escalated, Nickispy is triggered.
The next step is to track SMS messages, missed calls, aborted calls, and the geolocation information provided by the phone’s internal GPS. A Python script enables the bug to be triggered, which causes the browser to crash. This triggers the phone to execute the remote exploit code. The script then scans for the rest of the exploit code, the “egg.” A Python-based command and control server was written to handle the malware, partly due to the discovery that existing code in the wild was poorly written and failed quality assurance tests.
When Kurtz clicks on the fake “Carrier Update” link, the code that’s downloaded triggers the browser to crash and the phone to reboot. After the reboot, Nickispy can be spotted in the running apps list – it does not use stealth to hide itself. Immediately, Kurtz’s associate was able to demonstrate the phone’s location. After Kurtz places a call, his recipient (Alperovich) drops the call and sends an SMS to Kurtz’s phone. That enabled the attacker to track the SMS, and from that determine the location of the phone’s mic prior to the call being dropped. The attacker could then retrieve the last 15 seconds of the actual conversation prior to the call being dropped.