There will be two battles fought simultaneously in defense of Megaupload, the cyberlocker site accused by the U.S. of hosting and publicizing illicit copyrighted material. One is in the public arena, where we can expect the defendant to portray itself as Robin Hood, not so much stealing content from the rich as repurposing it for the poor, the meek, the 99%. It may even get some traction in that arena, but those same tactics may not play so well to a jury. That will be a separate battle whose defense strategy may not be so populist.

With the help of technology industry attorney Richard Santalesa and a team of researchers at New York City-based Information Law Group, ReadWriteWeb has examined the possible strategies a Megaupload defense may adopt, and analyzed their chances of success.
The Robin Hood defense
The case for Megaupload acting on behalf of the everyday consumer, the average Joe, is already being assembled; in fact, defense attorneys could perhaps sit tight, relax and watch the Web build their case for them.
Just after Megaupload first came under scrutiny by the U.S. Justice Deptartment, it pursued a business relationship of some sort with Universal Music Group. The subject was a prospective music download service called MegaBox. The indictment last week refers specifically to a November 2010 e-mail sent to one Megaupload proprietor from a UMG executive, listing the terms which MegaBox would have to meet in order for it to host music tracks copyrighted by UMG. For example, as the indictment quotes from the e-mail: “proactive fingerprint filtering to ensure that there is no infringing music content hosted on its service; proactive text filtering for pre-release titles that may not appear in fingerprint databases at an early stage; terminate the accounts of users that repeatedly infringe copyright; limit the number of possible downloads from each file; process right holder take down notices faster and more efficiently.”
The receipt of this e-mail could be cited as evidence that Megaupload was, at the very least, communicating with music industry executives about apparently legitimate business arrangements. Fast-forward to last month, when Megaupload announced it would launch MegaBox as a commercial site that would enable artists to distribute their music directly to listeners, while paying only a 10% distribution fee to Megaupload.
That started a wave of “question-mark” articles including this one from TechCrunch on Tuesday, plus this one from Digital Music News yesterday, and this one from Broadband DSLReports.com early this morning. Could the Justice Dept. have been serving as the stooge, the errand boy, for the music industry, stopping a competitive service from coming into being in revenge for the anti-SOPA demonstrations? We’re just saying, we’re only the messenger. (We present both the facts and the innuendo, and let you sort them out as a public service.)
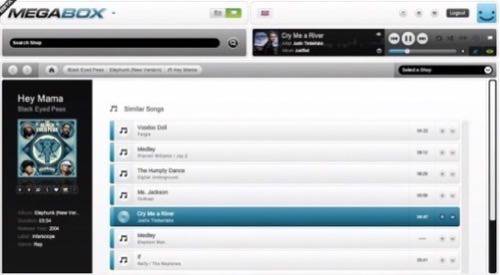
Missing amid all of the question-mark speculation was any recognition of the obvious connotation from this widely circulated screenshot, which features not some unknown, independent music artist seeking 90¢ from every dollar, but an album by The Black Eyed Peas, artists whose music is signed by, and who are promoted by, UMG. Regular RWW readers will recall UMG had successfully, if temporarily, used a DMCA petition to have YouTube take down a Megaupload promotional video featuring musical contributions by well-known artists, some of whom were UMG stars. A DMCA petition is normally used for claiming copyright violation, although the tracks these artists contributed, singing the Megaupload catch-phrase and theme tune, was not under UMG copyright.
So one potential Megaupload defense, which could be beta-tested in the public arena before being released to a jury, is that principal representatives of the music industry were leveraging the power of the justice system for anti-competitive purposes. For a judge to uphold any jury verdict in Megaupload’s favor arising from that defense, however, some type of direct conspiracy between the music industry and the government would need to be established beyond just sticking a question mark at the end of speculation. Here is where the bubble of question-mark would would need to be pierced, and speculation would have to give way to reality.
The existence of the one e-mail cited in the Justice Deptartment indictment indicates that investigators would have plenty of other Megaupload e-mails which may speak to the true intent of MegaBox, and the legitimacy, or lack thereof, of their intended business model, and their relationship with music publishers.
(Information Law Group, not unlike many smart vendors, declined comment on speculation.)
“Obviously Infringing Content”
If Megaupload’s attorneys intend to kick holes in the legal substance of the government’s case where they could do the most damage, they may take aim at the notion that the site had posted content that was obviously infringing. The so-called “safe harbor” defense applies to businesses that don’t police their users’ uploads, and therefore can’t tell whether content infringes or not. A service provider can’t be held liable for infringement if, in the name of maintaining privacy, it can’t see the infringement take place.
The indictment notes that Megaupload does not provide its own list of hosted files; instead, it relies on thousands of external sites to voluntarily provide lists. The implication is that the site intentionally created this wall of blindness to give itself a defense in case of indictment. That defense might just be effective, because it speaks to whether a legal standard exists for “obvious” (the notion that a child of 5 can tell the content was ripped off) and “infringing” (something that you can’t accuse the linking site of doing if it doesn’t host the content being infringed). In other words, if the link is not obviously doing the infringement, how can it be “obviously infringing?”

“Megavideo.com does purport to provide both browse and search functions, but any user’s search on Megavideo.com for a full length copyrighted video (which can be downloaded from a Mega Conspiracy-controlled server somewhere in the world) will not produce any results,” last week’s indictment reads. “Similarly, browsing the front page of Megavideo.com does not show any obviously infringing copies of any copyrighted works; instead, the page contains videos of news stories, user-generated videos, and general Internet videos in a manner substantially similar to Youtube.com. Browsing the most-viewed videos in the Entertainment category on Megavideo.com, however, has at times revealed a number of infringing copies of copyrighted works that are available from Mega Conspiracy-controlled servers and are amongst the most viewed materials being offered.”
Despite the links being hosted elsewhere, the indictment claims Megaupload was willfully infringing (and later, implies blatantly infringing) on copyright, with knowledge that it was doing so and knowledge of where the content was stored. The indictment does inject the notion of “obviously infringing content” into the discussion, by claiming Megaupload was working to make the infringement appear less obvious to itself. Is there a legal standard, however, for “obviously infringing,” and whose benefit would it serve to recall that standard?
InfoLawGroup’s Santalesa and his team cited the 2004 case of Corbis v. Amazon, where digital image warehouse Corbis sued Amazon “because the latter had hosted a vendor that was selling photographs that were under Corbis’ copyright,” as Santalesa tells us. “Corbis argued that Amazon should have been able to tell that the vendor was crooked, while Amazon argued instead that they had no reason to suspect that the vendor was in any way illegitimate.
The case was decided by summary judgment, he tells us, and the judge’s decision included this very telling description of how obvious an infringement has to be for it to be considered apparent:
“Congress’s discussion of apparent knowledge, and what evidence demonstrates such knowledge, is instructive. Absent evidence of its own efforts to notify a service provider, a copyright owner could establish apparent knowledge if she could show that an online location at which her copyrighted material was available was clearly a ‘pirate site.’… Pirate sites are ones that are ‘obviously infringing because they typically use words such as ‘pirate,’ ‘bootleg’ or slang terms in their URL and header information to make their illegal purpose obvious.’ Congress described the advertisement of illegal copyright activity through such slang words as a ”red flag’ of obvious infringement,’ and indicated that the infringing nature of sites containing such red flags would be apparent from even a ‘brief and casual viewing.’ Thus, once a service provider is aware of a site containing such ‘red flags,’ the service provider would have apparent knowledge of the infringing activity.”
To be obviously infringing, the judge declared, the flags have to be a particularly bloody shade of red. “In other words, an example of an ‘obvious infringement’ would be something along the lines of the infamous file-sharing site The Pirate Bay – it’s got the word ‘pirate’ right there in the title, and a cursory glance at the title would be enough for any reasonable person to conclude that they are reasonably likely to be involved in piracy,” Santalesa tells RWW. “With an example like Megaupload, it might be a bit trickier to prove the ‘red flag’ criteria, but the fact that they had the world ‘upload’ right there in the name of the website could be construed as such.”
Now, if one of these linking sites included a link that reads something like, “Mission: Impossible Ghost Protocol,” one might conclude that since that film was only recently released in theaters, it must be a pirated copy. But there are two other factors at play here. One is that, even if the content to which it links may be infringing, the link itself is just a link. Someone else produced that link, someone who may not be liable. Second, as anyone who actually clicks on links or reads a lot of email knows first-hand, links to things that look enticing are less often links to those actual things than they are to something else entirely. So evidence may need to be introduced establishing a kind of “causal link,” if you will, between the link someone else created voluntarily and the infringing content. Such an association might be necessary to establish that an ordinary user would trust that link to trigger a download of content the user would know to be infringing. Arguably, without the ink, the content would not be obvious at all.
One other possibility may be for the defense to apply the technological abstraction of the cloud to the contention that Megaupload knowingly infringed because it knew where the alleged illicit content was located. If it used cloud-oriented object technology such as CAStor to pool its storage from its many servers worldwide, only some of which were located in Virginia, then the defense could argue that Megaupload’s proprietors actually were not aware of either where or what the content was. What’s more, if they invoked hybrid cloud storage, then the defense could argue that it may be impossible to establish that Megaupload actually hosted the alleged illicit content at any one point in time.
Even if the Mega Conspiracy is found guilty in the end, the law will definitely be tested, especially where technology may have been used to stretch it to its limits.










