Web applications are still one of the greatest threat to enterprise security, according to Hewlett-Packard’s 2011 mid-year enterprise security risk report. This is no surprise, considering we saw data from Imperva in July that shows Web apps are probed or attacked at least once every two minutes. What is surprising is that enterprises have been slow to recognize and patch vulnerabilities, giving malicious hackers ample opportunity to penetrate their networks.

Weaknesses in Web applications make up 31% of all vulnerabilities, according to HP. Technically, reports of Web app vulnerabilities have gone down in recent years, but that is not necessarily a good thing. Legacy Web apps still provide a great risk to enterprise security.
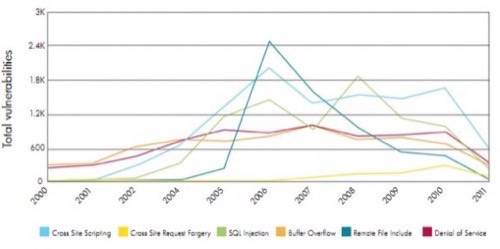
A lot of what HP presents in its report will not be new to security professionals. Every single security company and its long lost second cousin has a mid-year security report. For instance, did you know that cross-site scripting (XSS) is the compromises the most significant Web app vulnerability? Or that buffer overflow and Distributed Denial of Service (DDoS) attacks are the second and third most used vulnerabilities? If you are in the security industry, you certainly did know that.
HP founded a program called the “Zero Day Initiative” (ZDI) in 2005 designed to reward security professionals for responsibly reporting unknown vulnerabilities. Since 2005, Apple Quicktime has the most reported vulnerabilities with Microsoft Internet Explorer coming in second. Java, Firefox, Webkit, Real Player and Adobe (Shockwave and Reader) also make the list, along with HP OpenView. Those are some of the most fundamental technologies on the Web and their breadth contributes to the problem of enterprise security risks.
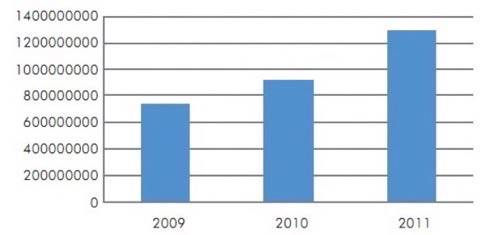
HP notes that it does not really matter if there are new vulnerabilities or not. Malicious hackers already have an ample surface of attack with existing vulnerabilities. Patching, closing, fixing, debugging, replacing software, installing security measures or any other method that can be done to fix those vulnerabilities across the entire enterprise landscape would cost hundreds of millions if not billions of dollars. Yet, considering the volume of attacks keeps on increasing no matter how many vulnerabilities are reported, it behooves industries to attempt to get their networks up to do. See the chart below for mid-year attack totals from 2009-11.
SQL injection (SQLi) attacks are very popular among “hacktivist” groups like LulzSec and Anonymous. Booz Allen Hamilton’s recent email leak was mostly SQLi related. The prevalence of SQLi attacks is laughable. Worming an SQL attack into a company’s server should be fairly simple to stop with a layered security approach that stops the data injection with firewalls or data sandboxes within the servers. It is a popular attack because it works. It works because enterprises either do not know what they are protecting against or have been too negligent in updating their security policies.
Check out HP’s entire report here (PDF).
What can enterprises do to close the gap between legacy vulnerabilities and Web application usage? As we have seen, the attack surface is wide, like a stretched-out cloth that can easily be penetrated by hackers who know what they are looking for. As Web apps become more critical to critical business functions, how can IT managers and the security industry shrink the amount of avenues that malicious hackers use to gain access to sensitive information?