Last week, leading security company McAfee asked a question of the security industry, “are we really protecting our users?” A lot of evidence points to the contrary. As can be seen in a new mid-year threat report from firewall maker SonicWall, consumer and corporate networks are larger and more vulnerable than ever. Yet, the battle against malicious programmers is not lost. It is a matter of common sense and evolution in security practices that will help protect companies and users from those that would do them harm.

“The days of just buying and anti-virus or a firewall program and just putting it on a PC are over,” said SonicWall’s VP of corporate development Ed Cohen. Enterprises and small and medium business need a more layered approach to security. Yet, the layers need to be more sophisticated. With the growing complexity of corporate networks, a new approach is needed.
“It is not just about blocking ports anymore,” Cohen said. “It is monitoring and securing the network from the application and endpoint level as well.”
SonicWall’s report cites the growing problem of securing networks from social applications and mobile devices. These are new problems within the last several years that corporate networks have not yet caught up with. Cohen uses the example of Facebook, which has become a necessity for enterprises. Yet, monitoring when, where and how employees Facebook or other similar applications is necessary for enterprise security. For instance, a business’s marketing department needs to use Facebook but it should not be allowed to use applications within the platform, like MafiaWars.
There is also the growing ubiquity of mobile devices and workers accessing the corporate network. That includes workers accessing work data from their smartphones or remote workers tapping in from unsecured connections.
“The more access that companies give, the more vulnerable they are,” Cohen said. “Yet, at the end of the day, access and productivity often trump security.”
Cohen advises that consumers, corporations and small to medium businesses become more proactive with security. That includes more monitoring of how and when users are accessing their work data, installing sophisticated anti-virus programs, next-generation firewalls and filters that look scan for spyware, spam, Web vulnerabilities etc.
“It always surprises me when a small business says that it has an anti-virus program but asks why it also needs to get a firewall,” Cohen said.
Cohn has four recommendations to effectively secure a business network.
- Protect the network – That classic fortress approach where firewalls, black lists and security programs monitor the network itself.
- Protect the endpoints – This includes securing computers making remote connections to the network, from using Secure Socket Layer and Virtual Private Networks to make sure that every smartphone, tablet or computer that can access work data has an anti-virus client.
- Back up data – This is an old standby credo of the security profession (or anybody that has ever used a computer), but Cohen says individuals and companies often do not do a good job of backing up data. There are a variety of new products and services that can help companies automatically back up their data in case of crash or breach.
- Use managed service providers – This is a trend in enterprise that has grown in the last several years, especially when it comes to mobile devices. If you do not know how or cannot effectively manage your network, hire somebody else to help you do it.
SonicWall has an interesting quiz about detecting phishing attempts that it says most people fail miserably. Head on over an take the quiz and let us know how you did. It is a lot harder to detect phishing than even sophisticated users think (this reporter got six out of 10 correct and apparently that is a good score).
Here is a sample of the quiz. Is this phishing or legit?
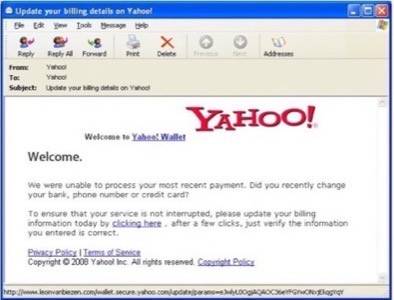
Answer: Phishing










