Bogus Twitter users do not have to steal accounts and tweet garbage about famous people to be menacing. Attackers use phony handles to Spam and scam unsuspecting users and send malicious links as well.

During Twitter’s “Red Carpet Era”, in October 2009 alone, the 140-character broadcasting service flagged twelve percent of all accounts as malicious and kicked them off, according to data from Dr. Paul Judge, a Social Network Security Research Team Leader at Barracuda Networks. Today, Twitter regularly flags two percent of accounts before giving them the boot. With legitimate users following and friending hundreds to thousands of others, a one-in-fifty chance of encountering an attacker is too great a risk to ignore.
David Geer writes about technology and the web. A native Ohioan and one-time ISP technician, he writes mainly about enterprise topics and his website can be found here.
“And what about the ones who are not caught?” asks Dr. Judge. The Barracuda expert estimates that as much as 70-percent of accounts are at least suspicious. Though the damage potential is disconcerting, the methods for spotting tainted Twitter connections are simple and effective.
Spotting Scammers
When a Twitter account follows a high number of accounts but does not have that many followers in return, it is probably a scammer who is trying to quickly build up followers by following many people and hoping that they will follow back. “A normal user follows the same number of people who follow them. But a scammer aggressively follows a lot of people,” Dr. Judge explains.
To address scammers, Twitter blocks users from following more than 2,000 people unless they have that many followers in return. Scammers try to beat this rule by following no more than, say, 1,100 to 1,200 users at a time while waiting for them to reciprocate. To stay under 2,000 follows and still build a following, scammers will unfollow all accounts that don’t eventually follow them and simply try following others. As a result, scammers who have not successfully built up a large number of followers may follow 1,100 people or so but have only 40 people following them.
The statistics of scammers who have been successful will be just the reverse. Though they started out with more friends in order to build up their followers, they now have plenty of followers. And because they need fewer friends to support that, they have unfollowed all but a few.
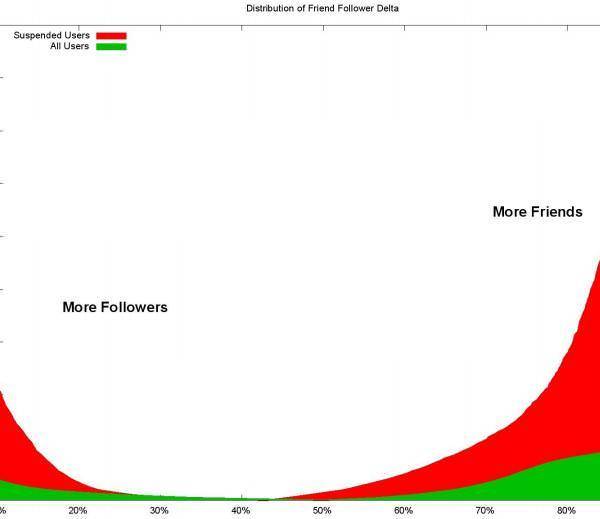
The green and red graph from Barracuda below illustrates this “Friend-Follower Delta”. The red area on the right represents accounts that Twitter cancelled for having too many friends and too few followers. The red area on the left represents accounts that had too many followers and not enough friends. Look for friend-follower numbers skewed to these extremes in order to pinpoint scammers.
Ferreting Out Fraudsters
“An account that tweets links and URLs with no text surrounding them is almost certainly a fraudster who is quickly distributing malicious URLs,” says Dr. Judge. Sometimes they include trending topics to ensure the tweet shows up in searches or a few words to convince people the link is an interesting article.
“In the end, it leads to a web exploit kit that attacks the user’s computer,” says Dr. Judge. Check a user’s recent tweets; if they fit this description, run!
Saying Good-bye to High Volume Vultures
Another way to recognize an attacker is by the volume of tweets they send. Scammers and fraudsters may send 100+ tweets-per-account-per-day as part of their onslaught. They use automated software tools that manage 1,000s of attacks from countless “users” all sending similar URLs at the same time.
“The average person does not have that much free time on their hands,” says Judge. But fraudsters may set up accounts over and over and burn through them quickly, sending astronomical volumes of tweets in a short time until they are caught, only to repeat the process in order to get their malicious links to as wide an audience as possible. If an account sends more tweets than any one person could, say good-bye.
Summary
On sighting skewed stats, lone links or tremendously high tweet volumes, a user need only avoid, block or unfollow the culprit to spare themselves a mountain of trouble.










