Who among us hasn’t received an email recently telling us to click a link to update our email account info, provide corrected banking login details, update our credit card information on file, and what-have-you? Most of you are savvy enough to know that these are phishing scams and don’t usually fall victim to clicking on these links or disclosing confidential information, but still stuff happens. According to SecureList.com, phishing messages accounted for 0.03% of all email messages this past April. And The Internet Crime Complaint Center reports nearly $556 million in losses to cybercrime in 2009, of which about half comes from phishing.

Ed Tittel is a freelance writer based in Round Rock, TX, who writes regularly on Internet and Web security topics. His latest security books include CISSP Study Guide, 5e, with James Michael Stewart and Mike Chapple, and Computer Forensics Jumpstart, 2e, with Neil Broom, Michael Solomon, and K. Rudolph. Check out his Website at www.edtittel.com or his tweets @EdTittel.
Anti-Phishing Technology to the Rescue
Given that there are substantial losses to phishing and these attacks continue to be incurred despite ongoing, detailed, and constant user awareness information from a variety of sources, all kinds of technical safeguards against phishing are now available to provide protection.
The majority of the more recent versions of the major Web browsers include anti-phishing protection:
- Internet Explorer versions include something called Phishing Filter (Versions 7 and 8) or SmartScreen Filter (Version 9) which relies on consensus reports about Web URLs and lists of known malware or phishing Websites.
- Google Chrome includes built-in phishing and malware detection, using Safe Browsing technology which applies advanced security settings and so-called “sandboxing” techniques (ways to keep the Web browser isolated from unauthorized access to information stored on your PC). This toolset also reports when it finds signs of malware on a Web site, or when the URL listed in a site certificate fails to match the site’s actual URL (a common sign of false representation).
- Firefox includes numerous phishing related security settings to stymie phishing attacks, including block reported attack sites and block report Web forgeries. Here again, this depends on checking lists of known bad actors and blocking them, and watching for suspect or unexpected behavior and reporting or blocking unwanted events from occurring.
- Safari employs sandboxing techniques to isolate Web content and applications from other information on systems, and also include malicious code blocking capabilities. As with the other browsers, Safari also relies on current reports about malicious and fraudulent Web sites to warn and protect its users.
These protections do have some value, but the problem with this approach is that phishing sites come and go with alarming frequency. A recent Trusteer report indicates that most phishing sites harvest the bulk of their ill-gotten information within one hour of their initial appearance online, well before most such sites register on reports and tracking lists that follow them.
In fact, security company Trusteer offers an innovative browser add-on called Rapport that significantly boosts browser security. It is designed to work with matching software components on bank and financial services Web sites to prevent phishing completely, and to block access to any and all information outside the Web browser while a user is accessing an account, updating sensitive information, or conducting any kind of financial business online. Rapport is also a sandboxing tool, but it is so stringent that users can’t even make screen shots of the software at work without creating exceptions to its default security rules (screen scraping is a well-used technique in keylogging and phishing attack software). Rapport even goes so far as to encrypt keyboard entries between user input and Web access, so that local keylogging software records only encrypted gibberish if and when a phishing attack is mounted against a protected machine.
Older browsers (IE 6, Safari 3, Firefox 3, and Chrome 7 or earlier versions) often lack built-in antiphishing protection. For these installations, various add-ins are available from MSN and Netcraft (some Web research may be required to find such old code, though, possibly even through the Wayback Machine). For current browsers, other add-ins worth investigating include BitDefender’s TrafficLight, BlueCoat’s K9 Web Protection, the CallingID Toolbar and the G Data CloudSecurity offerings that are all freely available online.
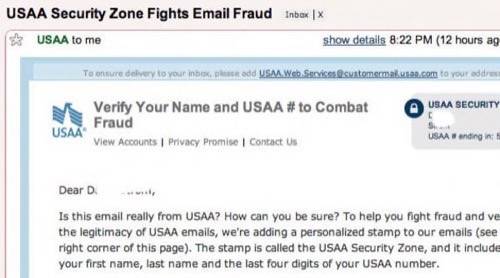
Other approaches are more savvy but less technology intensive. Insurance giant USAA, for example, now includes a personalized stamp called the USAA Security zone to all of its emails. It includes information that only USAA and the customer can know (see image) to verify its authenticity. The idea is to make it clear to recipients that incoming email is not fraudulent and can thus be trusted (and links clicked) to access account and other information. Expect to see more financial service providers of all kinds (banks, insurance companies, brokerages, credit card companies, and so forth) using such techniques to protect their users from fraudulent attempts to steal their information (and money) in the future.
USAA provides first and last name and partial account number data
Caveat Surfer!
Nevertheless, despite the best of technology, Internet users must remain aware that fraud is always a possibility, and to practice safe computing especially when they agree to provide account or other personal information online. Users should be trained to avoid clicking links in emails, and to pull up vendor or service provider Web sites directly, or to conduct sensitive financial transactions by phone. Though even these precautions do not totally eliminate all possibility of fraud they do bring it down to tolerable proportions.










