
Data security company Imperva released research today that says Web applications are probed or attacked 27 times an hour, or once every two minutes. At the peak of attacks, some Web applications see probes or attacks 25,000 times an hour, or seven times per second. The research gives concrete numbers to what security researchers, governments and enterprises have known for a while – their networks are persistently under attack.
When researchers look for malware and attack vectors, the tendency is to look for vulnerabilities in portals or code. Yet, most of the major data breaches in recent news have been the result of attacks on Web apps like email and data systems. The goal for hackers is to break applications with automated attacks searching for vulnerabilities until the apps crack and spill data straight into the hands of the hackers.
Imperva saw three distinct trends in observing Web app attacks from Dec. 2010 to May 2011: the attacks use four distinct strategies, they are automated and they originate in the United States.
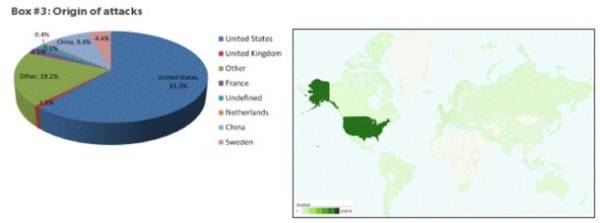
Imperva says that 61% of attacks originate from botnets in the U.S. Yet, that does not mean that those doing the actual attacks are located in the U.S. When botnet controllers are looking to hit a specific target, they want to use computers closest to their bounty. The important thing about the attacks coming from the U.S. is that a lot of American’s computers are infected with malware, thus part of some botnet. For instance, if hackers want to attack the U.S. government, the command-and-control center of the botnet might activate the 1,000 computers closest to Washington, D.C. About 10% of attacks originated from China, with Sweden and France also large contributors. China makes sense for its raw number of hackers while Sweden has some of the most universal and robust broadband in the world.
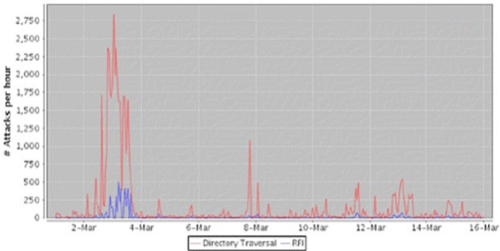
The large number of attacks stems from botnet automation. Imperva said that it sees patterns where applications will be attacked with heavy bursts of many thousands of attacks per hour followed by lighter periods of activity. In essence the criminal hackers are looking to break the application quickly by testing a lot of known vulnerabilities. If it doesn’t crack, their eyes turn elsewhere (criminal hackers are notorious for looking for easy targets). They automate the attacks before coming back for another look.
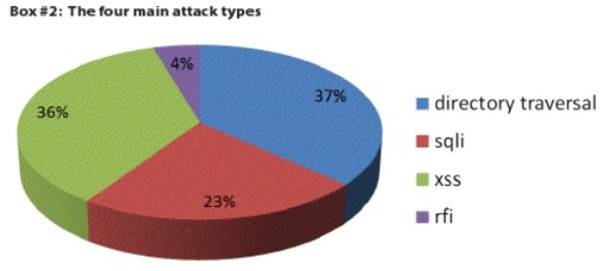
While Imperva was not specifically monitoring the Lulz Security attacks at their peak in June, they noted that they were very similar to what its research had turned up. A “hack” is an esoteric term. As far as the general public knows, the attacks were some complicated computer stuff that led to data being stolen. Yet, security researchers see four common types of attacks, what Imperva calls “the unfab four”: directory traversal, cross-Site Scripting, SQL injection and remote file inclusion (RFI). These attacks come in two waves: scan and exploit. An attacker may use directory traversal and cross-site ccripting during a scan phase and then hit it with an SQL injection or an RFI in the exploit phase.
Overall, Imperva’s findings are a great illumination of Advanced Persistent Threat (APT). The company recommends that agencies and corporations become familiar with how to stop deter automated attacks and perform their own “scans” to detect known vulnerabilities. If companies are on top of knowing their security weaknesses and communicate with the security community, APT attacks can be withstood and ultimately turned against the criminals perpetrating them.










