On April 15 the Obama Administration released its official report on a plan to safeguard online identities across the Internet that will protect individuals and entities and create a secure backbone on which to do business on the Web.

The National Strategy for Trusted Identities in Cyberspace (NSTIC) will be a department within the National Institute of Standards and Technology (NIST) that will work with the private sector to give Internet users a secure identity. The idea is to create an “Identity Ecosystem” – “an online environment where individuals and organizations will be able to trust each other because they follow agreed upon standards to obtain and authenticate their digital identities,” according to the report.
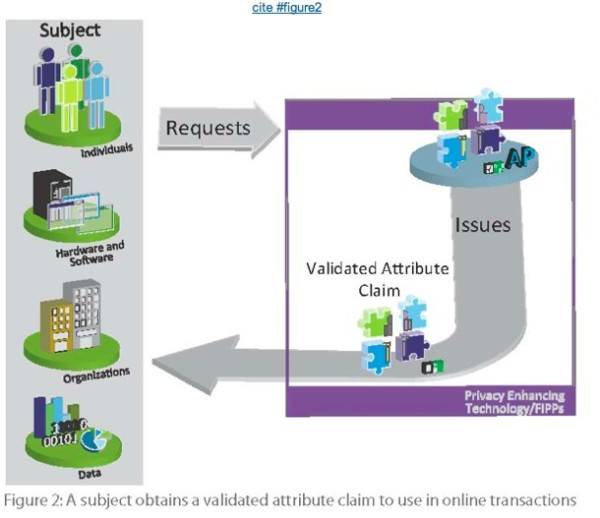
An example from the report:
Mary is tired of remembering dozens of user names and passwords, so she obtains a digital credential from her Internet service provider that is stored on a smart card. Now that she has the smart card, she is also willing to conduct more sensitive transactions, like managing her healthcare, online. One morning, she inserts the smart card into her computer, and uses the credential on it to “run” some errands.
The plan outlines the strategy for the Identity Ecosystem, which it says will be completely voluntary. Neither the federal government nor corporations can mandate that users sign up for the Identity Ecosystem; it is designed to ensure anonymity on the Web, especially for users that could be harmed if their true identity was known.
“The government will neither mandate that individuals obtain an Identity Ecosystem credential nor that companies require Identity Ecosystem credentials from consumers as the only means to interact with them,” the report says.
There are four guiding principles that govern the notion of the Identity Ecosystem:
1. Identity solutions will be privacy-enhancing and voluntary
2. Identity solutions will be secure and resilient
3. Identity solutions will be interoperable
4. Identity solutions will be cost-effective and easy to use
That stipulation comes as a big sigh of relief for some advocates and pundits who feared a Big Brother approach that would be mandated by the federal government. NSTIC is designed to allow the private sector to carve out the parameters Identity Ecosystem.
“Only the private sector has the ability to build and operate the complete Identity Ecosystem, and the final success of the Strategy depends upon private-sector leadership and innovation,” the report says.
That is a different approach from other countries, like Spain, where Bob Blakely, VP, distinguished analyst, and agenda manager for IT1 Identity and Privacy Strategies Service at Gartner, spent time earlier this year and noticed the complete opposite approach.
“The thing that really stood out for me was how American the NSTIC proposal is,” Blakley said. “Spain has, since 2006, has had an electronic identity card for all citizens. A number of the conversations I had with businesses and government entities is to how to get businesses to accept an identity credential that was produced by the government. NSTIC frames the problem exactly in the opposite way.”
There are a number of ways the Identity Ecosystem could manifest itself. From a “smart card” – digital identity – that houses your trusted identity, to smart grid authentication, to the ability to have bankcards or university ID cards validated as Identity Ecosystem-approved credentials.
The implementation of NSTIC could force some companies, like Facebook, to change the way it does business. Overall NSTIC is an ambitious agenda set out to create a more secure Web. For the idea to come to fruition it will take the cooperation of all the primary stakeholders involved, from the federal government to the tech companies and most importantly, the user.
“NSTIC paints a utopian picture of a user-centric identity management system in a business environment that does not commoditize on identity,” said Aaron Titus, the privacy director of the Liberty Coalition in a conference call April 18. “Of course, we support that vision but success is far from assured.”










