Editor’s note: We offer our long-term sponsors the opportunity to write posts and tell their story. These posts are clearly marked as written by sponsors, but we also want them to be useful and interesting to our readers. We hope you like the posts and we encourage you to support our sponsors by trying out their products.

In security, it’s pragmatism that counts. You don’t want to overreact in devoting company time, effort and finances on any security measures “just because”, but you definitely want to allocate these resources towards what is best for you. One way to do that is by understanding the varying rings of security that begin at your servers and expand outward to the walls of the data center itself.
At Rackspace, we like to picture hosting security as many layers building on top of each other. The foundation of good security is established in the data center. On top of that are layered the security preventions and protocols of the networking, device, OS, application infrastructure, application and business process floors.
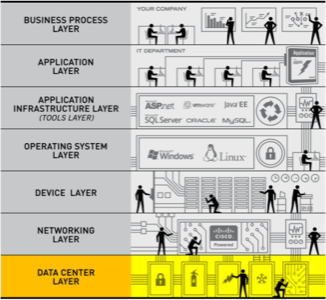
Each layer, or floor, of the security house has different considerations and best practices that should be accounted for. Regarding the data center layer, which is the subject matter of this post, two data center managers at Rackspace, Wayne Bell and Cormack Lawler, provided some helpful input.
A safe data center environment is established by concentric rings of security.
The outermost ring of data center security is comprised of the exterior of the actual center. The shell of the building is the most basic line of defense housing a data center in an unmarked building. Having cameras at entry and exit points and having no exterior windows onto the center’s floor are all ways exterior security can be tightened. In regards to data center physical security, Lawler says “you can either be the most threatening guy on the block” or be hidden entirely. Both options can work.
The second component of exterior armament is access. Who gets into the data center? This can be regulated through some basic means: ID checks at the door, no cameras or phones allowed within the building, no one allowed on the actual data center floor. Access can be even further restricted to sensitive areas within the facility by limiting which employees actually have to be there. For example, if those employees in charge of product supplies don’t need to be in the electrical room, then that access should not be allowed.
After the exterior of the compound, the power level comprises the next ring of security. Best practices for the data center industry are to have power enter facilities via underground channels. Additionally, power units should be encased in concrete conduits, and transformer units should be padlocked so only the electrical company has access. Once power enters the data center, electrical distribution rooms should become restricted access arenas.
The actual data center floor comprises the innermost circle of security. Bell points out that at the most simple level, “On the floor, security becomes a personnel issue.” If someone can physically get their hands on your server, they can access the information stored within it. A lot of the risk inherent to a data center floor can be mitigated by highly limited access. Enabling employees to self regulate also can contribute to a safer environment.
As we move through the different floors of the security hierarchy, each layer will form a foundation for those that come after it. Moving through an online environment layer by layer may help to isolate risk throughout the data center.










