Today at the RSA security conference in San Francisco, Microsoft’s Corporate VP of Trustworthy Computing, Scott Charney, spoke – opening his talk with this question: “Do you want anonymity or accountability? YES!”
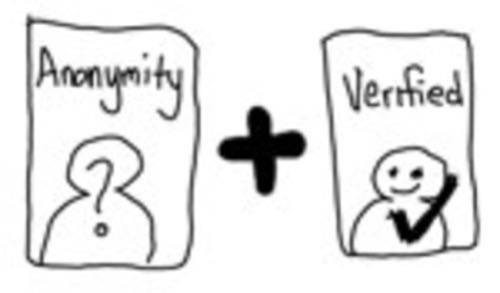
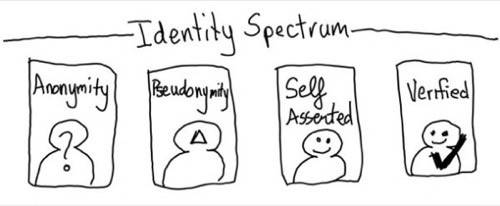
But how can you have both? I created a spectrum of identity to help understand the different forms that exist on the internet. On one end is Anonymous Identity. Basically you use an account or identifier every time go to a Web site – no persistence, no way to connect the search you did last week with the one you did this week.
This guest post was written by Kaliya Hamlin, also known as Identity Woman, who has been working on cultivating open standards for user-centric identity since 2004. She co-founded, co-produces and facilitates the Internet Identity Workshop, the primary venue for collaboration on identity standards amongst large Internet portals, large enterprise IT companies and small innovators.
Pseudonymous Identity is where over time you use the same account or identifier over and over again at a site. It usually means you don’t reveal your common or real name or other information that would make you personally identifiable. You could use the same identifier at multiple sites thus creating a correlation between actions on one site and another.
Self-Asserted Identity is what is typical on the Web today. You are asked to share your name, date of birth, city of residence, mailing address, etc. You fill in forms again and again. You can give “fake” information or true information about yourself – it is up to you.
Verified Identity is when there are claims about you that you have had verified by a third party. So for example if you are an employee of a company, your employer could issue a claim that you were indeed an employee. Or you might have your bank verify for your address.
A Linear Spectrum?
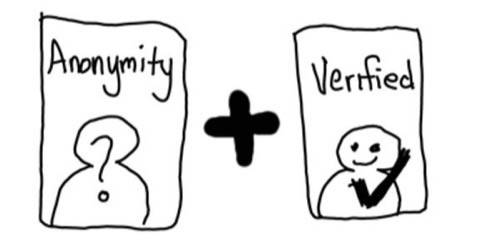
It seems like the two ends of this spectrum can’t go together. You can’t be anonymous and verify yourself by sharing all of the details on a credential from a government issuer who has asserted they have checked these things are true.
Microsoft demonstrated today how you can achieve anonymity and identity verification together at the same time, giving you verified anonymity. This technology (that relies on some pretty complex cryptography) lets you prove things without giving away too much information about yourself. For example:
- Proving you are over 21 without giving away your actual birth date
- Proving you live in a certain congressional district and are a registered voter but not having to give away your name or address
- Proving you are a kid at a middle school in San Jose without giving away which school or which grade you attend
Two years ago Microsoft surprised a lot of people with the purchase of Stefan Brands’ company Credentica and its product U-Prove. It promised to open up the intellectual property and make it available for everyone. Finally, two years later, it is opening it up under the Microsoft Open Specification Promise. If you want to understand the crypto you can watch an hour-long video of Dr. Stefan Brands explaining it .
Microsoft is releasing the reference SDK’s in source code (a C# and Java version) under the BSD open source software license. The goal is to enable the broadest audience of commercial and open-software developers to implement the technology in a way they see fit.
At the last Internet Identity Workshop there was a lot of conversation about Active Clients for all identity protocols: OpenID , SAML, WS-*, Information Cards, etc. Active clients support end users – regular people managing their different identities and credentials (like an over-21-verified, but anonymous ID). One way to make them usable is to map the underlying id management tools available online to real world metaphors – like the cards you find in your wallet. Information Cards are digital cards that are selected as one needs them to present online via a selector. The community has developed an open standard for exchanging information in this format in the IMI (Identity Metasystem Interoperability) Technical Committee,and is at OASIS.
Microsoft is releasing more IP under the OSP for the integration of U-Prove technology into “identity sectors” that other companies are developing. This includes the Higgins Project, which has the main open-source information card selectors.
As for its own products, the company is releasing to the public the Community Technology Preview (CTP) of the U-prove technology (as per the crypto spec), with Microsoft’s identity platform technologies (Active Directory Federation Services 2.0, Windows identity federation, and Window’s CardSpace v2). This video gives you a developer’s perspective of the U-Prove technology from the guys who have been building it for years.
The underlying cryptography, open standards used to exchange information, and the client-side tools to support end users will enable more Web services to take advantage of the full range of identities on the spectrum – not just the socially verified ID’s that services like Facebook or Twitter provide.










