While the MD5 hack that puts e-commerce sites at risk by faking security certificates received most of the attention at the 25C3 conference in Berlin today, another interesting talk about using XMPP to ensure privacy and security on social networks by Jan Torben Heuer caught our eyes as well. Heuer demoed a social bookmarking service named Diki, which implements some of his ideas, though in the long run, the developers are planning to take this prototype and develop a full-blown social network with a focus on privacy and encryption around this.

Heuer argues that ensuring privacy on social networks is almost impossible, due to the centralized architecture of these networks, where all your information is controlled by one corporate entity, and where the user has to simply trust the service provider without having any control over what this provider does with the information.
As an alternative, Heuer proposes to use a decentralized network based on XMPP, where data is only exchanged between friends and transmissions are encrypted. One might argue that XMPP still relies on servers, though it is surely a more decentralized system than the monolithic reliance on one service provider.
The talk mostly focused on the technical and privacy aspects of sharing semantic data like Friend-of-a-Friend (FOAF) information through an XMPP network, but it also introduced the Diki bookmarking and tagging application, which you can download and start from here.
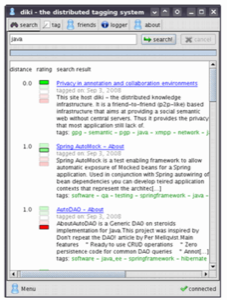
Diki
Diki is the first implementation of these ideas and is available as a Java application that allows you to create a new account, import your delicious bookmarks, rate your friends’ bookmarks, and which automatically encrypts your communication by using the OpenPGP standard. It’s clearly still a prototype, but it raises a lot of interesting questions.
If you want to delve deeper into this topic, you can download the presentation here (PDF), or read the actual paper (PDF). If you have some bandwidth to spare, you can also download this presentation and all others from this week’s Chaos Computer Congress from here.










