OAuth, the open authorization protocol standard that will let users give limited access to their data to third party websites without giving away their passwords, crossed an important threshold tonight.

All parties involved in building the spec have signed a covenant of non-assertion, meaning that OAuth can now be safely implemented anywhere without concern about Intellectual Property lawsuits. If you think this is too geeky for you – try out the live demo embedded below.
We celebrated Google’s addition of OAuth to all the Google Data APIs in July, but for all you cautious types out there – there’s not much excuse anymore. No more passwords are required and a greenfield for mashups is now wide open.
The parties that contributed to building OAuth and have singed the promise not to sue are: Yahoo, Google, AOL, Twitter, Ma.gnolia, Citizen Agency, Wesabe, Pownce and Six Apart. Also signing as individuals were Eran Hammer-Lahav, Mark Atwood and Blaine Cook.
What is OAuth?
OAuth is a standard protocol for one web site to access user information on another website without asking the user for their password, but accepting confirmation from the 2nd site that the person is in fact who they claim to be. As Eran Hammer-Lahav, Open Web Evangelist at Yahoo! and OAuth point-man, told us tonight: “It is a way to build distributed services across multiple vendors while still keeping your data as private and safe as you would like it to be. You can limit it, for example – for time (like only one day), only read access, photos only and not videos, etc.”
Why is this important? This is a key technical step towards making data portability real. It creates a path for users to move data they’ve created on one service into another service that can then offer new features or personalization based on what the users have exposed to them about themselves from elsewhere. It’s a big ingredient in a recipe for innovation, in the form of mashups or otherwise.
How is it different than OpenID? It’s a related, but different way to move data around. OpenID got a non-assertion covenant signed almost a year ago and provided, along with the Apache Foundation, the basis for the OAuth covenant. There’s a whole lot that can be done with both of these protocols and we look forward to seeing them develop together.
What does OAuth look like in the wild? Below are two examples. The first is a screenshot of Yahoo’s location based service Fire Eagle asking a user if they want to grant permission for another app to access their data on Fire Eagle.
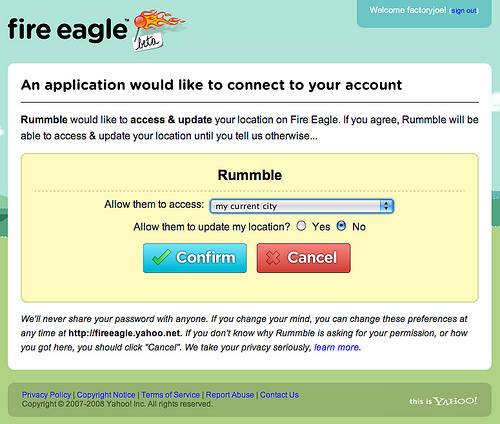
Screenshot from Chris Messina.
The second example is a mock live demo of OAuth in an iframe, created by Eran Hammer-Lahav. A detailed explanation of this demo can found here.
Pretty awesome, no? So let’s get the safe, granular data porting rolling! We eagerly anticipate a growing ecosystem of apps that do things with user data that were never possible before. As Eran Hammer-Lahav, who’s been working on this full time at Yahoo! almost all year, says – the web owes him a beer.










