Thanks to a more technology-savvy workforce, ubiquitous broadband, online collaboration, and social networking tools, it is individual workers, and not IT organizations, that are creating a new trend in business, a trend being called “technology populism.” Despite the rewards of using web-based tools and the ease-of-use they provide, this new trend has inherent risks as well. And any IT managers who are ignoring the new, open internet and the power it provides are also ignoring the risks and security threats technology populism brings to the strategically planned IT infrastructures that they have helped build.

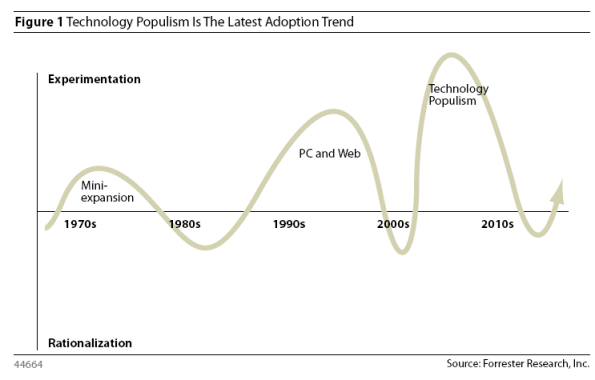
So, What is Technology Populism?
According to a new report by Forrester Research, Inc., Technology Populism is defined as “an adoption trend led by a technology-native workforce that self provisions collaborative tools, information sources, and human networks requiring minimal or no ongoing support from a central IT organization.”
For the layperson, this definition can be boiled down to this: more and more people are functioning as their own IT department at work.
History of IT Trends in Business
In the 1980’s and 1990’s, companies began bringing in minicomputers to replace the expensive and hard-to-maintain mainframe systems of the past, which in turn gave way to the rise of PC networks, LANs, and client/server based computing. The ease-of-use and cost of these new systems was a driving force powering the switchover that took place. Since the new web applications are also cheaper and easier than the current IT infrastructure in most traditional businesses, doesn’t it make sense that the next movement in IT would be to transition to web-based computing?
Not so fast! Before everyone fully embraces the web app/cloud computing initiatives, there are some things to consider. Although the users are happy with their new tools they provided to themselves, how is this impacting the business?
Real vs Perceived IT Needs
A company’s IT department generally provides a new user with computing equipment when they come onboard. More often than not, the equipment provided is a laptop computer and a web-enabled/email-enabled mobile phone device. The necessary tools and software programs the user needs to do their job are provided as well. Often, these include an Office suite of some sort, email, web access to email either via an VPN or secure web site, and remote access to their company’s resources. Additional security programs like anti-virus and/or anti-spyware are provided as well, but it’s unlikely the user will ever notice them, much less interact with them. In the background, IT stays busy making sure the computers and servers are protected and updated with the latest security patches, and the network itself remains uncompromised from outside intrusions.
However, today’s employee is no longer satisfied with these basics. In their personal life, they’ve embraced the world of always on connectivity, access anywhere, social networking, collaboration, and cloud computing. More of today’s companies are run by Gen Xers, and the growing population of Millennials (born between 1980 and 2000) in the professional workforce often dismisses conventional productivity tools like email in favor of text messaging, instant messaging, mobile devices, and social computing tools. These Millenials embody the Technology Populism movement bringing the tools they use at home like instant messaging, Facebook, Wikipedia,iPhones, BlackBerry devices, and even PlayStations to work with them. For example, Adobe told Forrester that one of its European CIO customers required PlayStation support because the firm had a handful of Millennials who used PlayStations instead of PCs. (And somewhere, an IT manager is turning over in his grave.)
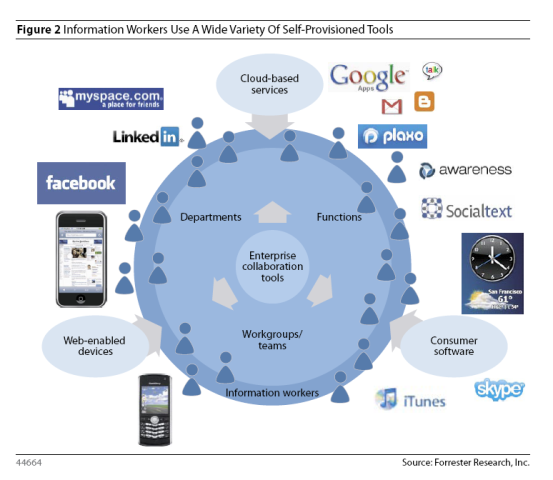
It might be that not only are the users more comfortable with the web apps they “grew up with,” it’s also possible that, despite their supposed tech-savviness, they don’t actually know how to use traditional enterprise software. Could it be that what the users actually “need” is training? Could they be turning to lightweight applications because they don’t truly grasp the complexities of or know how to use the software IT has provided? I would say that it’s more than possible.
A Microsoft executive recently told Forrester that 90% of the feature requests he gets for Microsoft Office productivity tools are already in the products. Since many users don’t even know the features of the software provided to them, they don’t see it as a loss to turn to a scaled-down online version. If anything, they think they’ve gained features since web-enabled apps offer different types of features than their desktop-based cousins. So if businesses are going to continue to insist that the users only utilize the software applications IT supports, then the business has a responsibility to make sure the users know how to use them. (I know plenty of people with a MySpace profile decked out with the latest flash widgets, but that doesn’t necessarily translate into a knowledge of how to perform calculations in an Excel worksheet!)
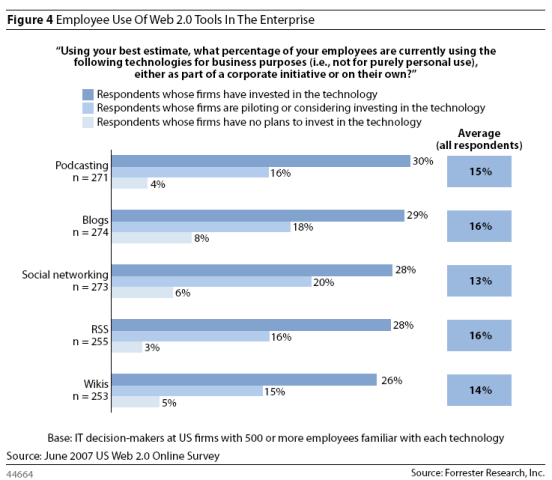
However, for some companies, the use of social computing technologies is fine, and their IT departments have even embraced their adoption in the enterprise. Forrester found that between a quarter and a third of employees at enterprises that have invested in social computing technologies corporate podcasting, blogs, social networking, RSS, and wikis are using those technologies for business purposes. Perhaps more significantly, decision makers at companies with no plans to make investments in web 2.0 technologies reported that, in the absence of a sanctioned corporate initiative, at least 3% of their colleagues are using them on their own. So, while web technologies are fine for some companies, it should not be up to the users to make that call – just because users want to use web technologies, doesn’t mean they should.
Companies dealing with non-public customer data, for example, have to meet certain compliance guidelines to ensure that sensitive data isn’t accessed anywhere outside of a secure connection. So what’s to happen when a rogue employee throws a spreadsheet of private data into Google Docs because it’s an easier way to share that large file with others than trying to compress it down to meet the size requirements of traditional email? Do you really trust Google enough to maintain the security of that file? What about the user whose Google password also happens to be “fido?” Their perception that the ease-of-use of Google Docs outweighed the security need to have their exchange of data processed over a secure connection and logged by their internal servers. Is this acceptable? Most IT managers would say, “heck NO!”
Tech Populism Concerns
Some IT managers have concerns about the introduction of more web technologies in the workplace. For example, what is to be done when a web app goes down? (It happens). Does business stop as well?
There is also a concern about what Forrester calls an “information silo.” New tools like wikis and blogs could create “micro-silos” where locating the information or people you need becomes near impossible. Already, companies with in-house databases and extensive Sharepoint web sites are dealing with requests from staff looking for information, and the information they need is all in one place. I can’t even begin to count the number of times I had to answer the question “where is that file on Sharepoint?” It’s on Sharepoint! Argh! Now imagine that in addition to the company intranet, data is spread out across the web living on blogs, wikis, podcasts, videocasts, and social networks. How will you find it then? And will multiple versions of the same file reside out there as well?
And what about the burden on IT support? IT departments are trained to thoroughly understand, control, and support the hardware and software they provide to their staff. Adding more and more niche applications to their support workload isn’t necessarily wise.
In speaking with an IT Network Manager in the finance industry, he explains, “the IT department in each company is already the most complex support environment in the history of business. We can easily have 100 different applications to support with just the basics of Windows, Office, and business applications. We need to maintain a minimal and consistent software installation, containing programs which are commonly used throughout the business world. We do not have the time or resources to train and hand-hold new users to our company because they want to use Firefox, Google Docs, or whatever the next ‘Super Web 2.0 Ajax’ program is. In other words, just because the perception of IT staff is that we have a ‘Neo in the Matrix’-like understanding of technology, we can’t possibly know and support every online application.”
But Is IT Support a Necessary Component to the Equation?
The traditional provisioning model has business needs translated into a set of software categories and requirements that lead to lengthy evaluation processes, implementation, deployment, training, and hopefully use. IT plans for days, weeks, and even months in some cases to deploy the new technologies. And then there is the user training. An architecture firms IT director recently explained, “Our users would rather have teeth pulled than sit through software training; they just dont show up.”
Although traditional technologies like Exchange-based email and calendaring, Microsoft Office, industry-specific enterprise applications, or Sharepoint services for online collaboration and document sharing may require user training before mastery, a typical user can master a web app in minutes, without extensive training or with just a little help from colleagues and friends, not IT.
So What’s an IT Manager to Do?
More than anything, IT Managers need to realize that the power of individuals to provision their own applications, information, and social networks is a trend thats unlikely to stop. They can block sites on their firewall, but as users venture out on laptop computers beyond the company’s walls, those sites become accessible again. Some employees who work mostly in house have taken to utilizing the company-provided aircard to circumvent the restrictions of the LAN. Then there are the web services themselves -they are aware that businesses are blocking them internally, so they’re offering other ways to get access. Facebook, LinkedIn, and Plaxo, for example, are all offering mobile versions of their web services.
For an IT manager to successfully balance the risks and rewards of technology populism, they must first embrace the trend to move forward, then they must address their particular company’s exposure levels. They need to determine who is using social tools and why. It may be that they need to focus on simplicity, usability, training, or speed of their current set of applications, and perhaps even address the needs of some individuals or groups to fill in the gaps that the online tools are addressing. Is the Marketing Department using an online wiki? Then perhaps it’s time to train them on how to use Sharepoint Services’ wikis instead.
The IT manager needs to stay current with what’s happening in the business IT world, yes, but also in the consumer web application space as well. Company policies need to be written up to address the use of social tools and guidelines need to be put in place about the sources of trusted information.
It may also be time for IT Managers to give some web apps a try. Web apps like Spiceworks offer an in-house installation of a web-based inventory analysis program, and could be a good alternative to the static, manual databases used in the past. IT Managers will need to determined which tools they sanction and which tools need to be avoided, while ultimately keeping not just their department’s needs in mind, but the needs of the business as a whole.
In the end, it’s the IT Manager who will determine where the company stands in regard to Technology Populism, and that may be one of the more critical decisions a business will make in the coming days and months as Tech Populism becomes the new reality.










