Web Security
firm Finjan has just released their Q4 2006 report on web threats, which
includes describing two cases of web 2.0 hacker attacks, on Wikipedia and MySpace. What’s
more, the report says that hacking the Web is very much a commercial activity nowadays –
which is keeping Web security companies like Finjan on their toes heading into 2007. The
report also makes some predictions around web security for 2007.

You may remember that R/WW covered the Q3 Finjan
report, which outlined threats to Web 2.0 and Ajax websites. The Q4 report extends
that theme and notes that the dynamic nature of the Web complicates security going into
2007. It states:
“2006 saw the arrival of a diverse range of web-based infection techniques —
including rogue anti-spyware, ransomware, and rootkits — that elude traditional security
solutions geared to protect against email viruses and spam. Another development in 2006
was the commercialization of malicious code, as financial motivations played an
increasing role in the evolution of malware. Motivated by financial gain, hackers are
trading vulnerabilities in online auctions, commercializing products such as malicious
website creation toolkits, and developing new distribution techniques, including spam,
for the propagation of malicious code.”
Finjan predicts that in 2007, Web 2.0 platforms and technologies will increasingly be
used by hackers as a “legitimate” tool for distributing malicious code. Also they predict
that, as Windows Vista and Internet Explorer 7.0 begin to achieve critical mass, this
“will likely trigger a new wave of exploits from professional hackers who have had time
to prepare in advance for this scenario.”
Two Hacking 2.0 Cases: Wikipedia and MySpace
Regarding the two specific Web 2.0 cases discussed in the report, the methods used
involved spam and phishing. Firstly here is the Wikipedia case:
“This scam was detected and published by Sophos in early November 2006. Taking
advantage of the fact that Wikipedia allows anyone to create and modify articles, hackers
uploaded an article to the German edition of Wikipedia (de.wikipedia.org) including a
link to a fix for a supposedly new version of the Blaster worm. However, the “fix” was
actually a piece of malicious code. Sophos discovered the scam by intercepting spam
messages directing recipients to the Wikipedia article with the malicious code.
Alerted to the problem on their site, Wikipedia immediately fixed the page with the
malicious link. However, according to Sophos, the previous version of the page was still
present in the archive and continued to point to malicious code. This allowed the hackers
to continue to send spam pointing to the archived page on Wikipedia, and infect victims’
computers. Wikipedia later confirmed that it had permanently erased the archived version
of the page.”
And the MySpace case:
“In another incident reported in early December 2006 by Websense, hackers compromised
the MySpace social networking site and infected hundreds of user profiles with a worm.
This malicious code exploited a known vulnerability to replace the legitimate links on
the user profiles with links to a phishing site, where victims were asked to submit their
username and password. In addition, according to Websense, the worm embedded infected
video in victims’ user profiles.”
Finjan writes that Web 2.0 has “opened the door to new propagation methods for
malicious code.” They also claim that since the vast majority of these sites are
considered “trusted” or legitimate by URL Filtering products, “they will not be blocked
despite the fact that they contain malicious code.” Finjan notes that the term ‘infection
by proxy’ was coined to describe this attack vector using Web 2.0 sites.
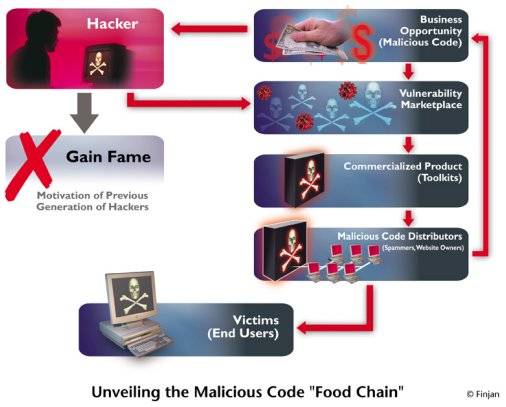
Hack for Dollars
What’s perhaps most concerning about this report is Finjan’s contention that hackers
nowadays are focusing a lot on web-based infection techniques – and that a commercial
market has evolved around this. Whereas in the ‘old days’ the motive of hackers was to
gain fame, today it is all about the money. Indeed Finjan says that commercialization
of malicious code was the most significant trend in the web security arena during
2006. Here’s a graph from Finjan illustrating this:
So this is something to be wary of for web apps and service providers. Along with Web
2.0, we now have Hacking 2.0 to contend with!





















